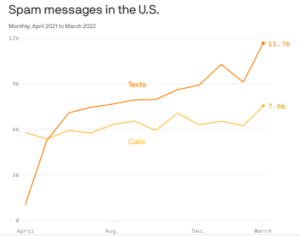
 Yes, you are getting hit with more spam emails and calls — and now spam texts — than at any point in the history of these devices. These messages are frequently dangerous! They often try to steal your data, identity and/or money — and the crooks are getting better and better.
Yes, you are getting hit with more spam emails and calls — and now spam texts — than at any point in the history of these devices. These messages are frequently dangerous! They often try to steal your data, identity and/or money — and the crooks are getting better and better.Surviving the Scam Surge
 Yes, you are getting hit with more spam emails and calls — and now spam texts — than at any point in the history of these devices. These messages are frequently dangerous! They often try to steal your data, identity and/or money — and the crooks are getting better and better.
Yes, you are getting hit with more spam emails and calls — and now spam texts — than at any point in the history of these devices. These messages are frequently dangerous! They often try to steal your data, identity and/or money — and the crooks are getting better and better.
 Testimonials have always been an important part of marketing. Today, in our digital world, online reviews are critical. Many prospects check for reviews on Google or Facebook before they even visit a company’s website.
Testimonials have always been an important part of marketing. Today, in our digital world, online reviews are critical. Many prospects check for reviews on Google or Facebook before they even visit a company’s website. Today passwords are a part of our everyday life. It is critical to protect our information from getting into the wrong hands. Unfortunately, a weak password is a weak defense against hackers. Here are a few ways hackers are trying to get a hold of your information and how you can help stop them.
Today passwords are a part of our everyday life. It is critical to protect our information from getting into the wrong hands. Unfortunately, a weak password is a weak defense against hackers. Here are a few ways hackers are trying to get a hold of your information and how you can help stop them.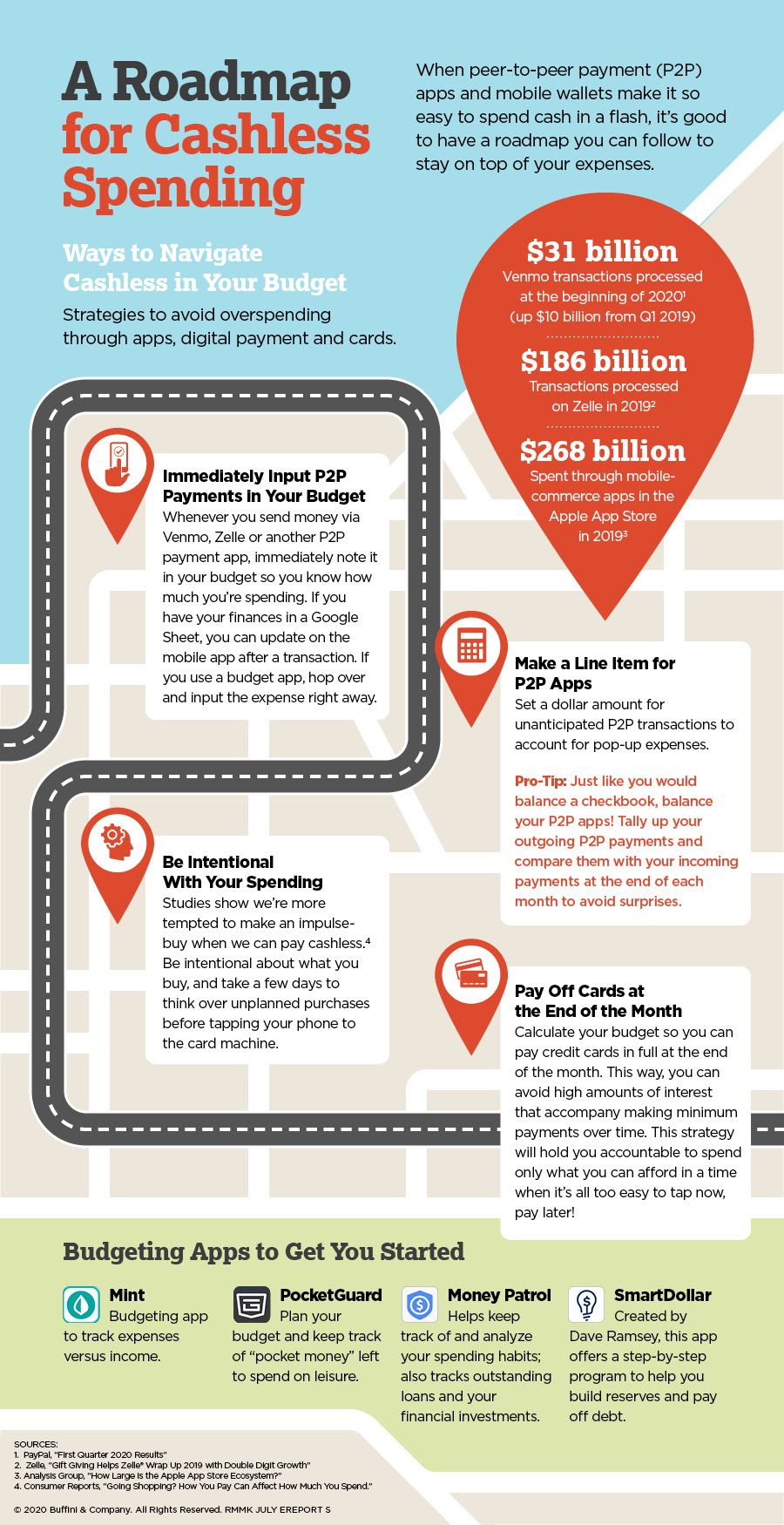

 How does your prospect or client KNOW that you are the expert they’re looking for?
How does your prospect or client KNOW that you are the expert they’re looking for?